These social engineering examples show how successfully criminals can use interpersonal influence to achieve their goal. This can be the handing over of hardware or the access to buildings. There are many incidents that confirm that these attacks are carried out in practice. The number of unreported victims is, it is assumed, many times higher.
To be prepared for the advanced social engineering attacks, we have taken the trouble to select more sophisticated attacks. Social Engineering is also called Social Hacking. However, the procedure of professional attackers is more extensive.
It is partly about pretending identities and obtaining free services. However, intrusion into IT systems is also one of the criminals’ targets.
-
Example 1: Shoulder Surfing & Dumpster Diving
The first social engineering example has little to do with IT systems. The bigger problem is the exploitation of the inattention of the users*. In shoulder surfing, usually in public space, the target person is looked over the shoulder.
The laptop is not always protected with a privacy film when working. This allows the person sitting next to you to collect valuable information in preparation for an attack.

But also dumpster diving is a very non-technical approach to successful social engineering attacks. This is about stealing garbage cans. If sensitive information is not shredded, it is the jackpot for the criminals.
Even strip cutting is not sufficient destruction for sensitive documents. A particle cut makes it almost impossible for criminals to recover the documents.
-
Example 2: Pretexting
In order to successfully carry out a social engineering attack in a business context, preparatory work is necessary. An outline of this is already shown in example 1.
But to increase the probability of success of an attack, the so-called pretexting can be used. In doing so, the focus is primarily on human emotions and needs:
Pretexting involves contacting the victim. But the message addresses at least one emotion or need. With this, the attacker aims to make the victim decide against the rational, correct action. The consequence can be the disclosure of sensitive information.

Those who put more effort into it create false identities in the context of pretexting and, if necessary, also operate false profiles in social networks and on dating portals.
From the private context, the grandchild trick is a now well-known scam in the form of pretexting.
-
Example 3: Call ID Spoofing & voice manipulation
After extensive information has been collected and the first contact has taken place, the next step is to build trust and remove barriers. The criminal pursues this goal to the detriment of the victims.
Call ID spoofing is used, especially in money fraud. The Caller ID is the telephone number of the person calling. With Call-ID spoofing, the phone number of the person being called is manipulated.

The most successful fraud scam from the private context is the police fraud. Strangers call with the 110 mainly senior citizens and give a pretext why cash or valuables must be handed over. However, this procedure also occurs in a business context.
Anyone who sends out a payment notice, especially if it is not the sender’s usual e-mail, has little chance of success. The chances are better if a call is announced in the e-mail.
If the actual number of the person to whom the number originally belongs calls, the chances of a successful scam increase.
You are currently viewing a placeholder content from Default. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
By reducing voice quality and limiting it to the bare essentials, criminals are driving successfully. Does the imitated person have an unusual voice? Then it helps to use voice manipulation software. The first successful scams have now come to light.
-
Example 4: Reverse Social Engineering Attack
In the reverse social engineering attack, the victim is motivated to contact the fraudster. The criminals’ creativity is great in this respect. The simple step would be to prepare an e-mail informing the victim that the service provider for ticket processing has changed.

For this reason there is a new e-mail and telephone number. If the victim now opens a ticket, the “new” service desk will be contacted. Afterwards it is agreed that the data causing the problems must be sent or the computer must be picked up by an external service provider.
-
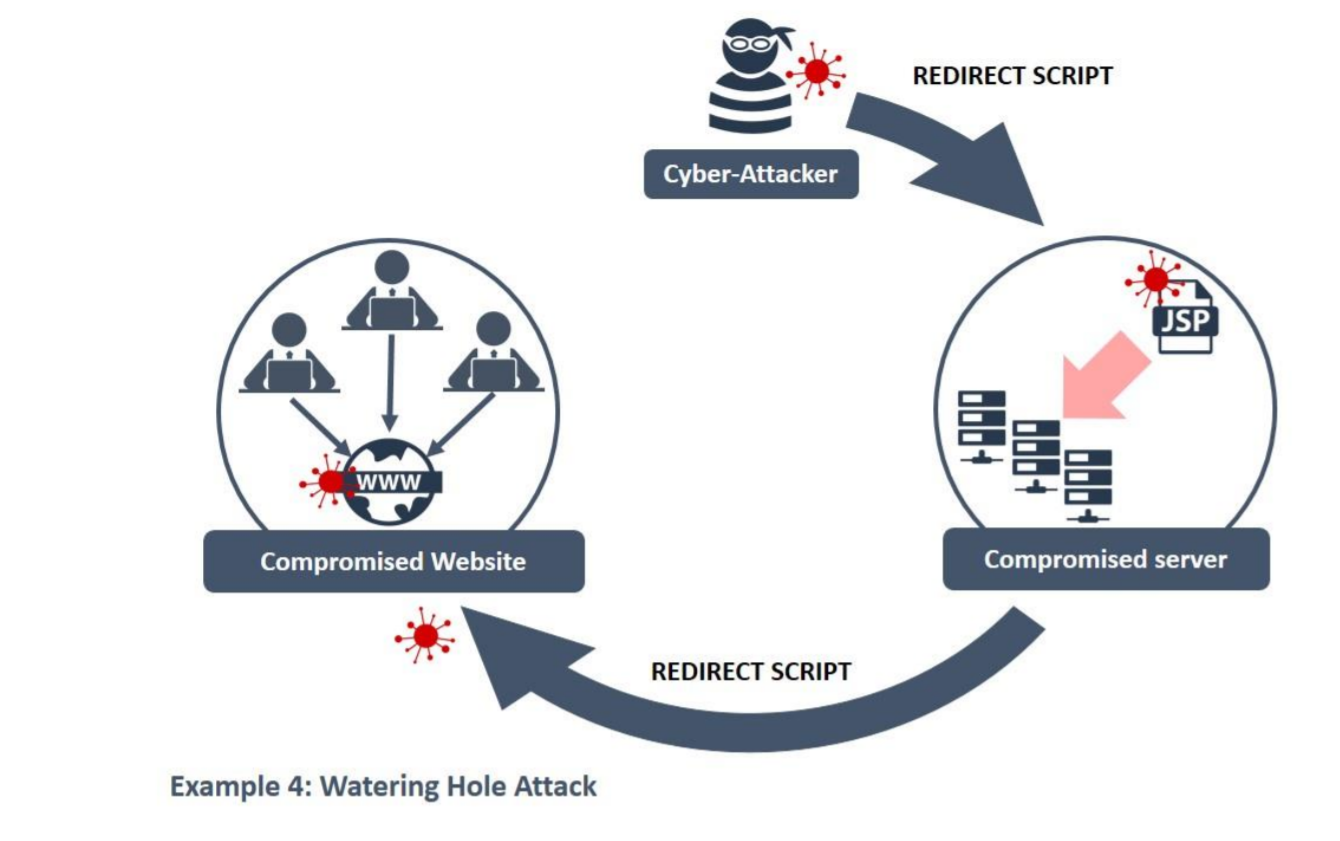
Example 5: Watering Hole Attacks
The “waterhole” attack also relies on the victims’ employees. The water holes that the victim is supposed to fall for are located on popular or frequently visited websites.
If it is known that the employees of a company have to visit a website frequently, e.g. to open tickets, to authenticate themselves or to look up information, this can be used to prepare a Watering Hole attack.

The popular website is being searched for a security vulnerability. A vulnerability that allows to inject Javascript or set up redirections.
If the target group visits the website, the placed forwarding is used to infect the victims with malware on the following website.
This procedure is complex and rarely found. However, it is effective because third-party sources, popular and frequently used websites can rarely be blocked in the corporate policy.
Advanced social engineering examples that anyone can fall for – or ?
The success of a social engineering attack depends on the effort of the attackers. If professional attackers invest a lot of money to attack, the chances are good that they will succeed.
The common phishing and spearphishing attacks have been omitted in this article – even though they can cause considerable damage such as with Wempe or Norsk Hydro.

