Am I infected with emotet? The most successful malware family has been causing headaches for businesses, individuals and organizations since 2018. Emails in your own name, expired data, good looking emails. When infected, many questions arise – but often whether it is emotet or other malware. EmoCheck is a tool from the Japan CERT (Computer Emergency Response Team) and enables the detection of an infection.
Emotet is distributed via phishing mails with Word attachment
The attack style of Emotet is certainly not new. But it is particularly well made. The subject of the different emotet mails ranges from an alleged invoice, shipping notifications, an invitation to a party or even information about the corona virus. Once infected, the malware uses its own account to send further, so-called dynamic phishing mails. This scam is particularly successful. The Bundesamt für Sicherheit in der Informationstechnik warns several times. But it is not done with emotet alone. Other malware such as Trickbot and Ryuk is downloaded and executed in the background.
Am I infected with Emotet? Run the EmoCheck now!
One of the features of Emotet is that it creates a semi-random folder after infection. You can find this folder under %LocalAppData%. It is only semi-random because it is made up of two words from the following pool:
duck, mfidl, targets, ptr, khmer, purge, metrics, acc, inet, msra, symbol, driver, sidebar, restore, msg, volume, cards, shext, query, roam, etw, mexico, basic, url, createa, blb, pal, cors, send, devices, radio, bid, format, thrd, taskmgr, timeout, vmd, ctl, bta, shlp, avi, exce, dbt, pfx, rtp, edge, mult, clr, wmistr, ellipse, vol, cyan, ses, guid, wce, wmp, dvb, elem, channel, space, digital, pdeft, violet, thunk
As shown in the picture below, Emotet is installed in the “symbolguid” folder. Both words can be found in the upper pool.
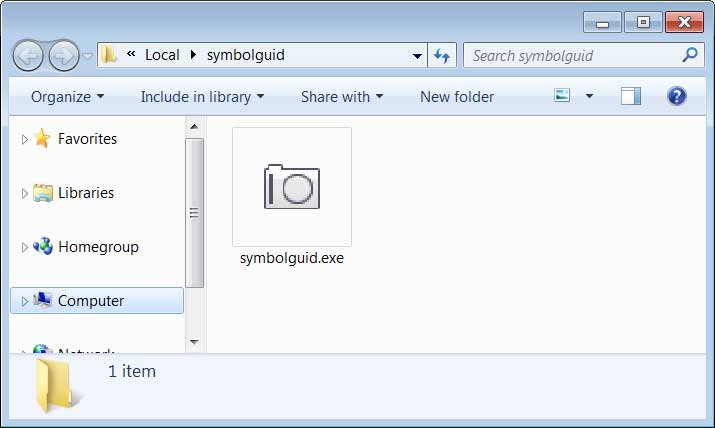
EmoCheck can be used to avoid manual testing of the infection. The tool can be downloaded easily. You can also download it from the GitHub repository. Once downloaded, simply unzip and open the file. Once the tool is released, you will get an alert in the terminal. Afterwards you can read the process ID and the place where Emotet has settled down.
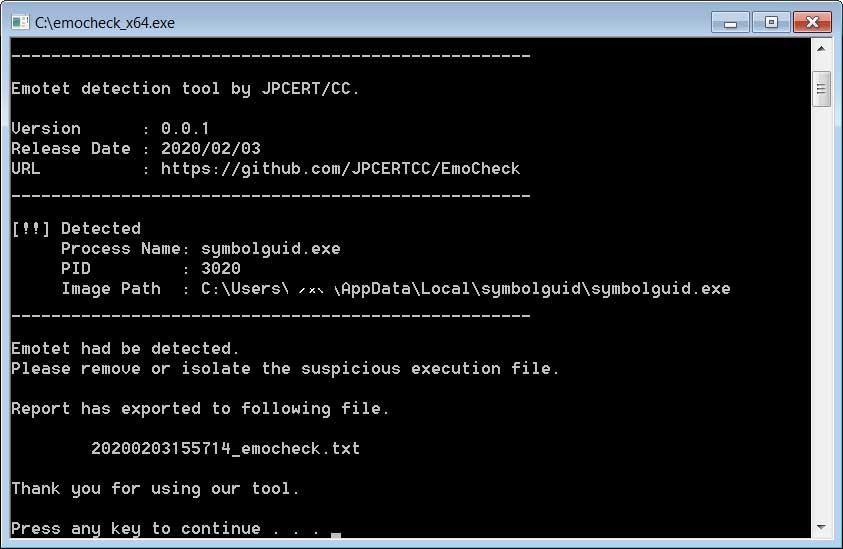
This information is also written to a log file. You can find this where the executed emocheck.exe is located. There the file is sorted by yyyymmddhhmmss. If the infection is positive, the Task Manager should be opened immediately and the process should be killed. Afterwards an antivirus scan of the machine is highly recommended. This small tool is useful for network administrators. Here it can be integrated into the login process. Infected machines can be identified quickly and a major outbreak can be prevented.

