All channels that have made it their business to report against new malware, scams and dangers are warning against the GermanWiper Ransomware. As is so often the case, everything starts with an application. Then the malware takes its course.
Data is deleted – GermanWiper overwrites everything with zeros!
For many it is the last chance to get back their data: To pay the ransom. In the past there was also ransomware where this actually worked. However, those affected by GermanWiper cannot count on this method to work. Ransomware overwrites the files with zeros and then changes the file extension.
Especially application letters are successful – they arouse curiosity and therefore do not even have to be sent to the personnel department. A click on the supposed curriculum vitae downloads the ransomware from the servers and begins the encryption process.
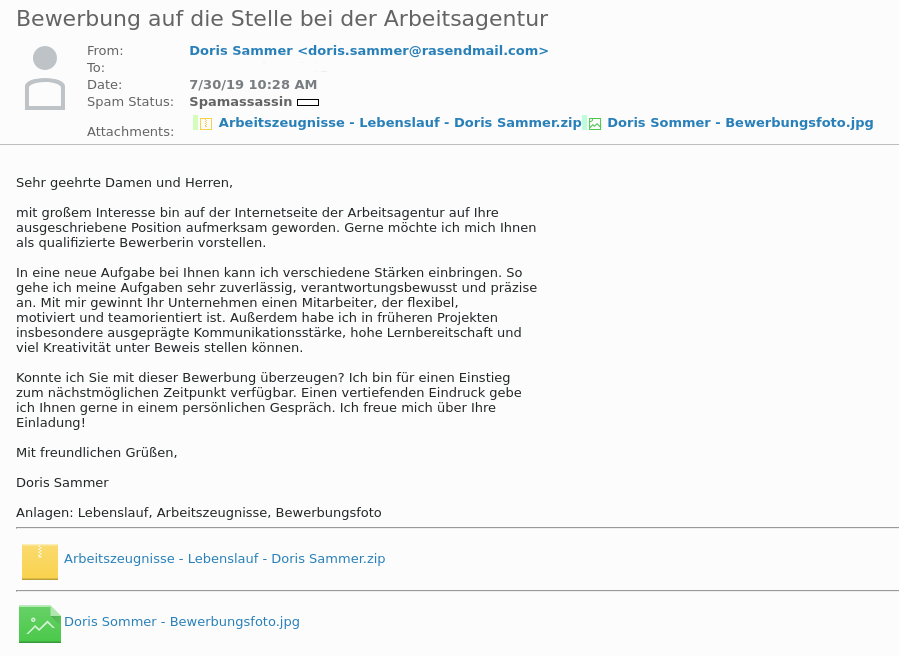
Job application gives no reason for skepticism – awareness is required!
If the application is free of errors, the e-mail address is classified as reliable and the position should have been filled long ago, it can happen quickly – the reader opens the attachment. Only after all data has been irretrievably deleted does the blackmail note appear.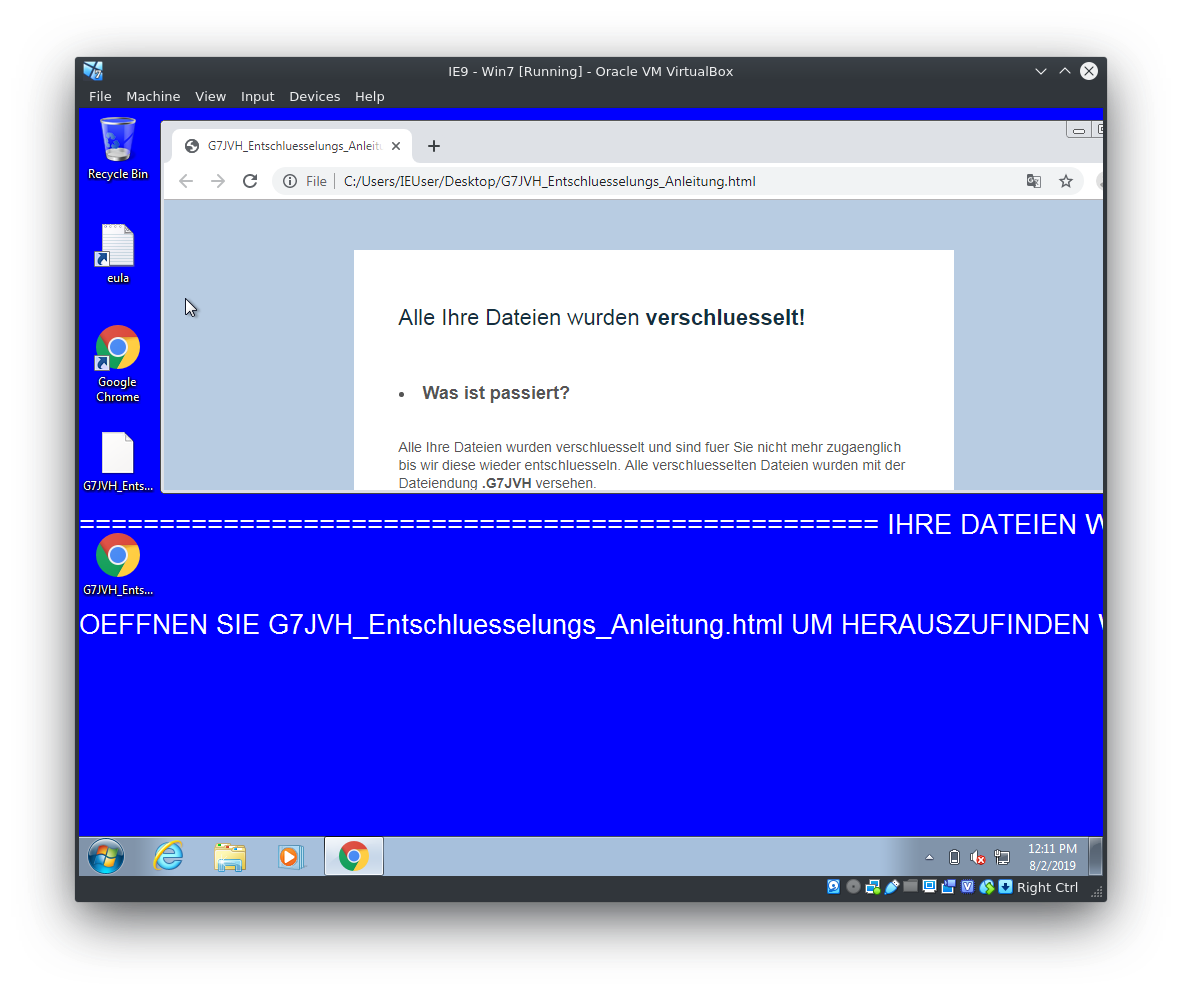
At this point we have to warn you again that paying the extortion money with GermanWiper does not bring back the data! This is what is being warned about on all portals that have taken up the cause of warning against ransomware, malware and fraud.
You are currently viewing a placeholder content from X. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
Protect yourself from GermanWiper – create backups!
The only reliable protection against GermanWiper is a sophisticated backup strategy. If you want to play it safe, you can proceed according to the 3-2-1 backup principle.
- At least three copies of the data should be available. These should not all be physically on-site or permanently connected to the infrastructure.
- The data should be stored on at least two different types of media. Here one can rely on different storage technologies and media types.
- A backup copy should be stored at one different location. Especially in the event of natural disasters an external location is worth its weight in gold.
In the end, however, this is only one of many backup strategies – the important thing is that there is a backup.
GermanWiper – attentive employees are the best protection!
Especially when the e-mail sounds professional, the job advertisement is accurate, technical security mechanisms have been overcome, the last line of defence decides – and that is the human being. It is therefore important to regularly educate people about new malware campaigns – and it does not always have to be an all-day training course. Often one morning or afternoon event every six months is enough for certain target groups to remain sensitized.

