DNS stands for Domain Name System and is one of the most important services on the World Wide Web. Since it has such a central role, it is very important that it is configured properly. Incorrect configurations can cause errors as well as serious security vulnerabilities.
What exactly is DNS?
The DNS can be considered as the phone book of the Internet. For example, if you want to call up the website of AWARE7 GmbH, you enter aware7.de in the address line of the browser and are redirected to the website as expected. However, there is a lot more going on in the background that end users don’t even notice. This is because the DNS translates the domain name into IP addresses. Since people are better at remembering names than numbers, as with a phone book, the DNS is a simplification for humans, so to speak.
As a normal Internet user, one hardly notices the IP addresses behind the web pages, since almost every web page has a DNS entry and can thus be translated. This has the advantage that IP addresses can be changed relatively risk-free without users noticing anything, since they only have to address the unchanged DNS name. With the help of the Domain Name System, a reverse resolution of IP addresses is also possible. This process is comparable to searching for the corresponding name in the phone book with a known phone number.
What happens if the configuration is incorrect?
If the Domain Name System is configured incorrectly, this can have serious consequences. It can cause websites to become inaccessible and like invisible. In analogy to the telephone book, this would correspond to a situation where there is no number or a wrong number behind a name and the person is therefore not reachable. However, such an error is not uncommon.
A well-known example of DNS misconfiguration includes the outage of service provider Cloudflare in July 2020. An article from heise explains the situation at the time in more detail. A DNS problem was also initially suspected in the prompt outage of Facebook services. However, it turned out that the problem was with a different protocol: the Border Gateway Protocol (BGP). An article from Cloudflare explains the Facebook case with some background and a blog post.
Security and DNS
Since the Domain Name System is a central component of a networked IT infrastructure, falsification of DNS data can be a starting point for attacks. There are different types of attacks related to DNS, but usually the main goal of the attacks is to lure the user to a fake website through DNS manipulation in order to subsequently grab confidential data.
This attack can be executed locally on the victim’s computer. On Linux and macOS systems, there is the /etc/hosts file. Manual entries can be created in this file, which are then interpreted by the Domain Name System. In the following image you can see how an entry has been created mapping the domain aware7.de to the IP address 142.250.186.142 . The special thing is that the IP address does not belong to AWARE7 GmbH, but to Google.
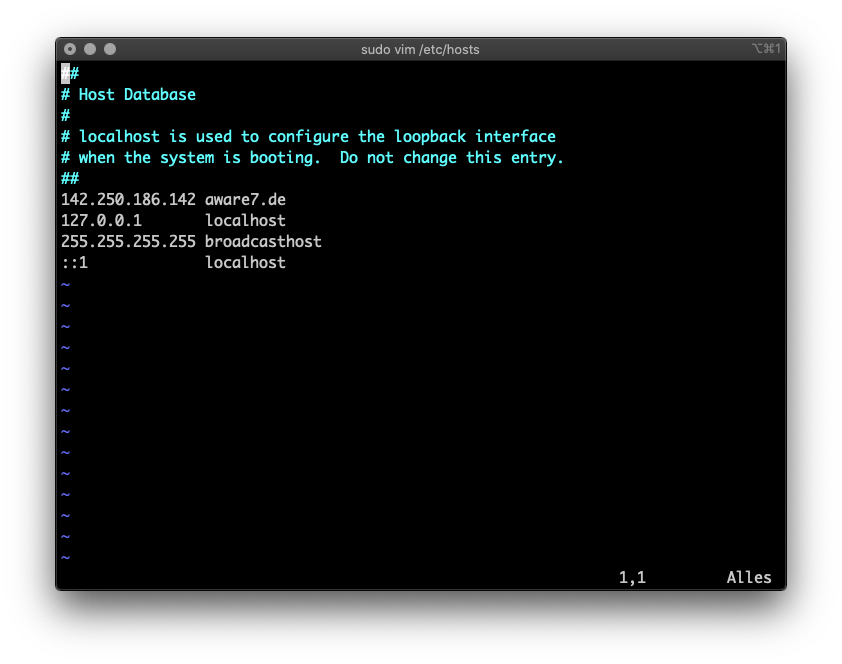
Due to this manipulated entry, the user no longer receives the website of AWARE7 when entering aware7.de in the browser, but instead a website belonging to Google. In the following video it is shown that the multiple call with aware7.de does not provide a correct web page.
A potential attacker could use this attack method to lure the victim to a fake website of online stores like Amazon or even Ebay. This is known as DNS spoofing, which we have already published a blog article about, explaining the attack scenario in more detail.

