At irregular intervals it happens that the success of a cyber attack brings whole companies to their knees – now a hacker attack has driven Swisswindows AG into insolvency. The St. Gallen-based company has already suffered an extensive cyber attack last year, which had its consequences until early 2020.
Successful cyber-attacks cause millions of damages worldwide. Consideration for hospitals during the pandemic is not taken. The lack of resources to pay blackmail money is acknowledged by cyber criminals with mercilessness.
A series of unfortunate events leads to insolvency
170 employees* are affected by the sudden departure of the company. After filing for bankruptcy, even the mayor was surprised. In a first step, business partners were the main recipients of information. The workforce was informed at a meeting.
Thus, in May 2019, a massive cyber attack led to a severe setback. A production downtime of over a month was accompanied by massive consequential costs. This incident had caused the company to come under “severe distress”. Further events have now contributed to the company’s inability to survive.
Detailed information on malware and incident handling is missing
Which malicious software drove Swisswindows AG into insolvency is not publicly known. Even if the suspicion, due to the long production downtime, is a encryption Trojan, this suspicion cannot be substantiated. The handling of the malware itself is also unknown. Companies like Norsk Hydro have dealt with the incident in their own company in a very transparent manner.
It is not the rule that the companies’ actions are due to a specific IT security incident. Another case that has caused a lot of attention is VFE-Mail. At the e-mail provider, all hard disks containing the customer’s content were deleted. A missing backup strategy made it impossible for the company to recover the data.
Ransomware threatens the survival of companies
It is no secret that the outbreak of a ransomware infection can cause considerable damage in a company. On the one hand the ransom – on the other hand the downtime. More and more corporations (from Alphabet to Tupperware) in the United States are now explicitly listing this risk in documents. These include, for example, annual and quarterly reports and those on special events.
This is due to various reasons. One reason is the increased amount of money needed for decryption. Thereby, times in which only 500 USD were demanded are over. It is not uncommon for decryption fees of 100,000 USD to be charged. A data recovery can become even more expensive with 210.000 USD.
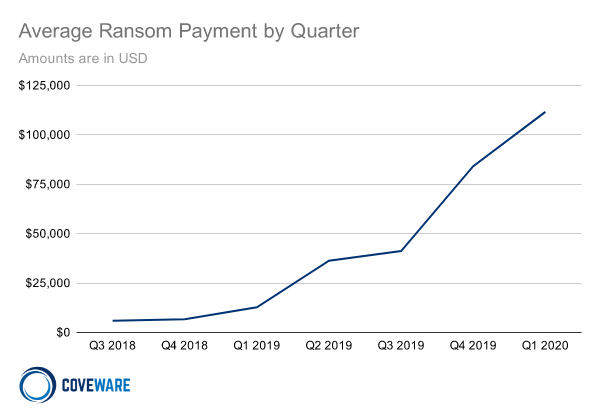
But it is not uncommon for the follow-up costs to catch up with you. The decryption of the data often takes several days. After the successful cyber attack, failures due to missing turnover have also caused problems for Swisswindows AG.
Cyber Security starts with prevention!
The first steps that companies should take in cyber security are clearly in the area of prevention. Rudimentary processes to handle successful attacks should of course be in place – but if prevention is lacking, the number of attacks becomes too large for incident handling. Successful security measures on a technical and human level can close numerous attack vectors. Reactive incident handling can be reduced to a few incidents. Insights can be used to sharpen preventive mechanisms.

