At first it looked as if Google’s popular streaming player had developed a life of its own – but the blame for the sudden playback of a video is the so-called CastHack. Two long-standing security holes in the device were exploited for this purpose. Two hackers are behind the attacks and wanted to use the action to draw attention to the problem. They could also have caused much more confusion.
The CastHack was done by j3ws3r and Hackergiraffe!
- “That’s no problem”
- “the vulnerability is only theoretical”
- “Theoretical risk with little practical relevance”
IT security people often have to listen to these or other phrases when drawing attention to problems. However, some gaps are also good for exploiting them to draw attention to the problem. Hackers have succeeded in doing this. The press speaks of thousands of devices, it itself of more than 100,000 devices on which the following picture was displayed:
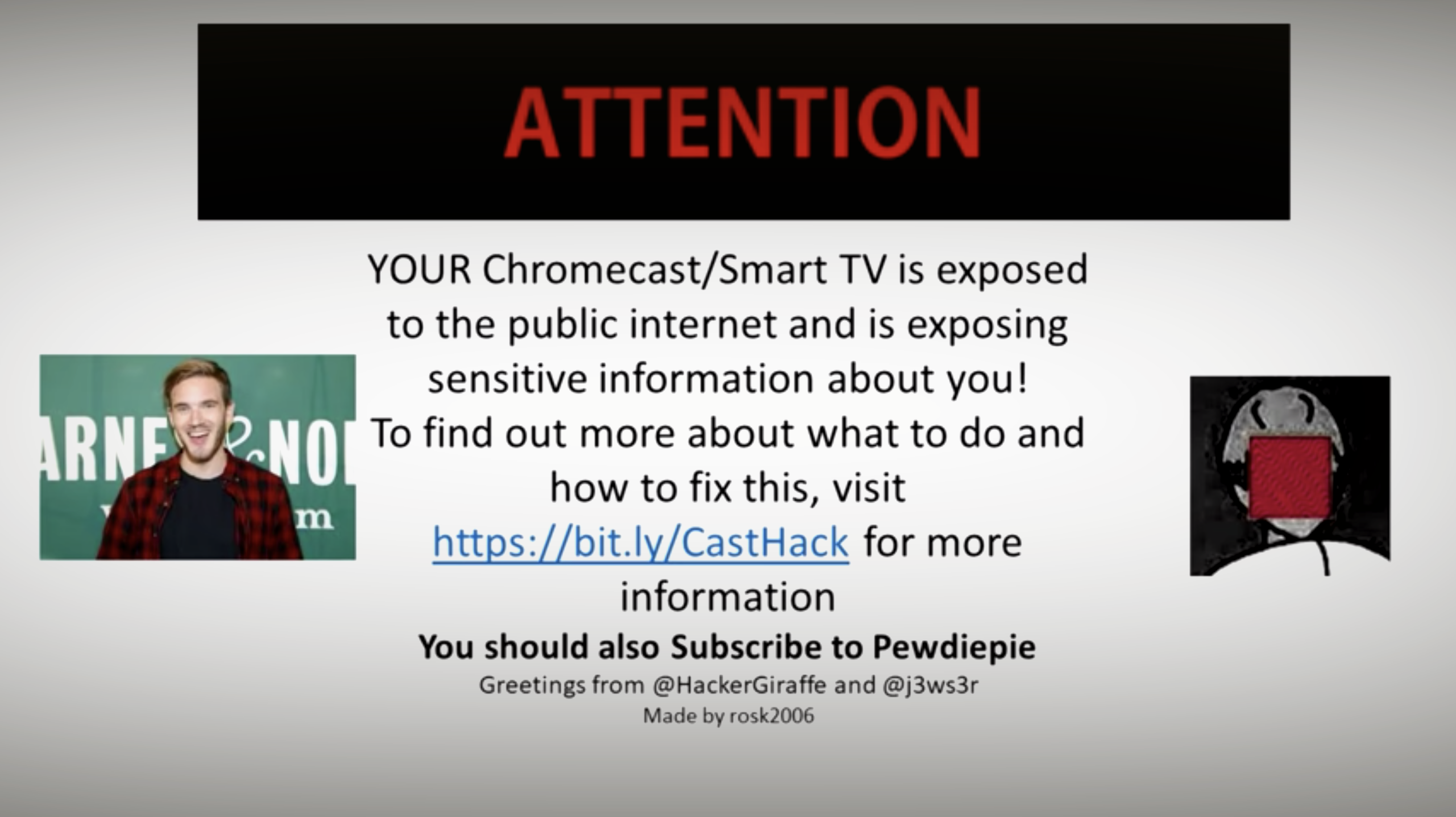
Why the CastHack could be done!
The hackers were able to exploit the CastHack due to two security vulnerabilities. One of them is the way Chromecast can get the configuration of the network settings. The first guess was that there was a problem with UPnP (Universal Plug and Play). This cannot be because the Chromecast does not use UPnP, but mDNS. As with many IoT devices, this process works without user interaction.
Known vulnerabilities from 2014 and 2016 now clear the way for CastHack. Unauthenticated Requests” can be sent to the device. This allows the device to be reset to factory settings, for example. This should not be possible, if only from the local network. However, if the chromecasts are set directly to the Internet, external control is possible. Probably the error lies in the router configuration of the Internet Service Provider of the affected user. However, the availability of the devices on the Internet can also have another reason. An infection with malware could be another reason. For example, a previous infection with malware.
The geographical distribution of available chromecasts confirms this assumption. It is probably a problem for Internet service providers, as most devices are located in the ASIAPAC room. In Germany, according to the Internet of Things search engine Shodan about 650 devices can be reached.

If a device is freely available on the Internet, a so-called deuth attack can take place. The successful attack causes Chromecast to lose its connection to the Internet. The device then returns to setup mode. Attackers can now play media content on the device, reset it or assign a new name.
Large-area actions provide for fast closing of the CastHack security gaps.
The Hacker Duo meant well. Malicious attackers could have used this template for criminal purposes. For example, the playback of audio signals would have been a possibility. Language assistants like Alexa or the Google Assistant could have been activated by the CastHack attack. In the meantime, the hacker giraffe has withdrawn from public life. At the end of last year public printers were already hacked by the duo. Requests were printed to follow the YouTube account of PewDiePie. Also at the CastHack the hint, as shown above, is placed.
https://twitter.com/HackerGiraffe/
The quickest way to eliminate this risk is to disable ports or their forwarding on the router: No hands, no cookies. Ports 8008, 8443 and 8009 should be disabled. The old saying also applies to this countermeasure: as much as necessary, as little as possible.

