Not much works on the Internet without passwords – but whether you always use the same passwords is very rarely checked. Criminals have also long since acquired a taste for this and therefore carry out the so-called “credential reuse attacks”. Once attackers on the network have found the login data and email in old stolen records, or have been able to spy on them, this attack is readily used.
Passwords are a problem – using always the same passwords is a much bigger problem!
The problem of passwords has been discussed many times on this blog. Thinking up long passwords on the fly that are random and long is not easy. It goes without saying that you should not forget the passphrase, but it is also not easy. For this reason, there are numerous ways to attack the password.
These are especially effective when the same passwords are used multiple times. An example of this is the credential reuse attack. In this attack, various online services are tested within seconds using a tool written by the attackers themselves. If a login is successful, this is logged. Using tools is faster, because this way you don’t have to check every website manually.
A former tool to show this was for example Cr3d0v3r, which is still freely available on Github, but does not work anymore. Cr3d0v3r is a small tool that wants only a little information from the user and then executes the credential reuse attack. Previously, the software discussed here went through the following steps:
- It is searched in public data thefts for the specified email address
- In addition, databases and pastebins are searched for the password that was stolen at that time
- The information found can be used to check access on other websites
If you are allowed to use the tool as part of a penetration test, the following scenarios may arise for you, but for this the tool must first be brought to a functional state through your own programming:
- Check if the found or handed over emails show up in data leaks
- Check where the email address is still registered to find out if the same email is always used
- If passwords are found, you can see if they are used at other websites or services
Programming knowledge is necessary!
Unfortunately, however, this no longer works, as the search for whether or not there are leaks for your given email address no longer provides any functionality. This is because the operator of the haveibeenpwned.com website has updated the API functionality to a newer version. Further, costs are now provided for the use of the API, as some users with too many requests have abused the API. The key to use it costs $3.50 per one million requests.
Also, it is possible to use Cr3d0v3r without the prior verification with your own password list. This must be passed as a TXT file. It is also possible to simply enter the password yourself. After that, the tool checks through the most common websites and tests whether an email / password combination was successful.
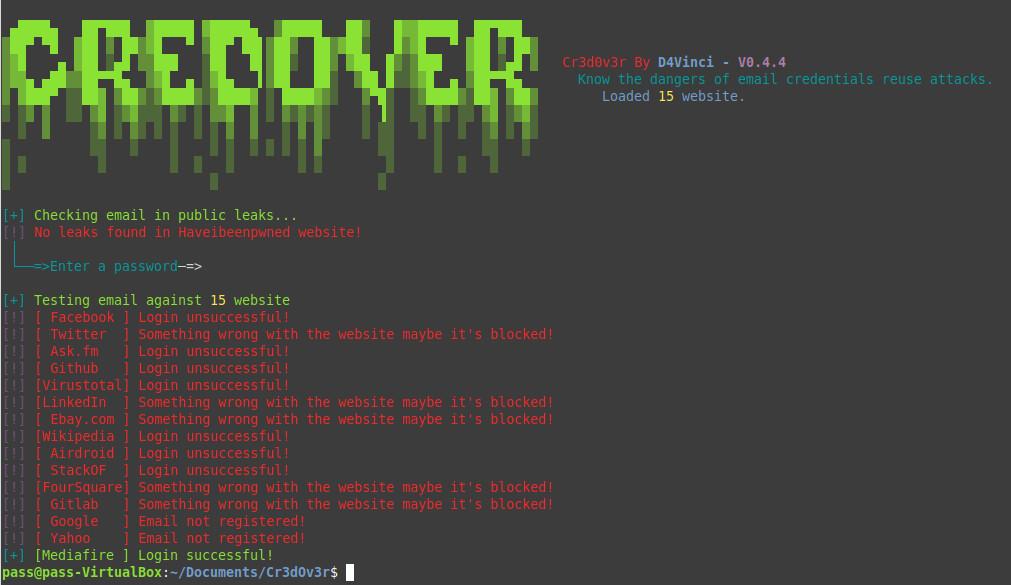
It turns out that users who use the same passwords everywhere can be hacked quickly. This makes it particularly easy for attackers to take over your account on the various platforms. If the attackers also have access to the email account, it is usually impossible to recover the account.

