Today is World Back up Day! A data backup is often the last chance. When a natural disaster occurs, a database crashes or data is encrypted by criminals – then often only a backup helps. Time to talk about backing up our so important digital content.
Important content can include corporate documents that must be retained, such as invoices. But also application documents, tax returns or children’s pictures are valuable digital goods. Restoring data, on the other hand, is quite expensive and often not worth the effort for private individuals. A backup protects!
No back up available?
Every second user already got to know the problem!
With the advent of smartphones and tablets into everyday life, a well thought-out back-up strategy does not get any easier. How do I regularly back up data from my devices combined with maximum convenience? This question is not so easy to answer. If the 2018 figures from the German Federal Office for Information Security are still up to date today, only 29% back up their smartphone every day. Apart from securing the smartphone, there are other precautions that should be taken in case of loss.
More than two-thirds of users would have to live with outdated back-ups if the devices were lost or refused service. By the way, the top 4 reasons why you can no longer access your data/data backup are:
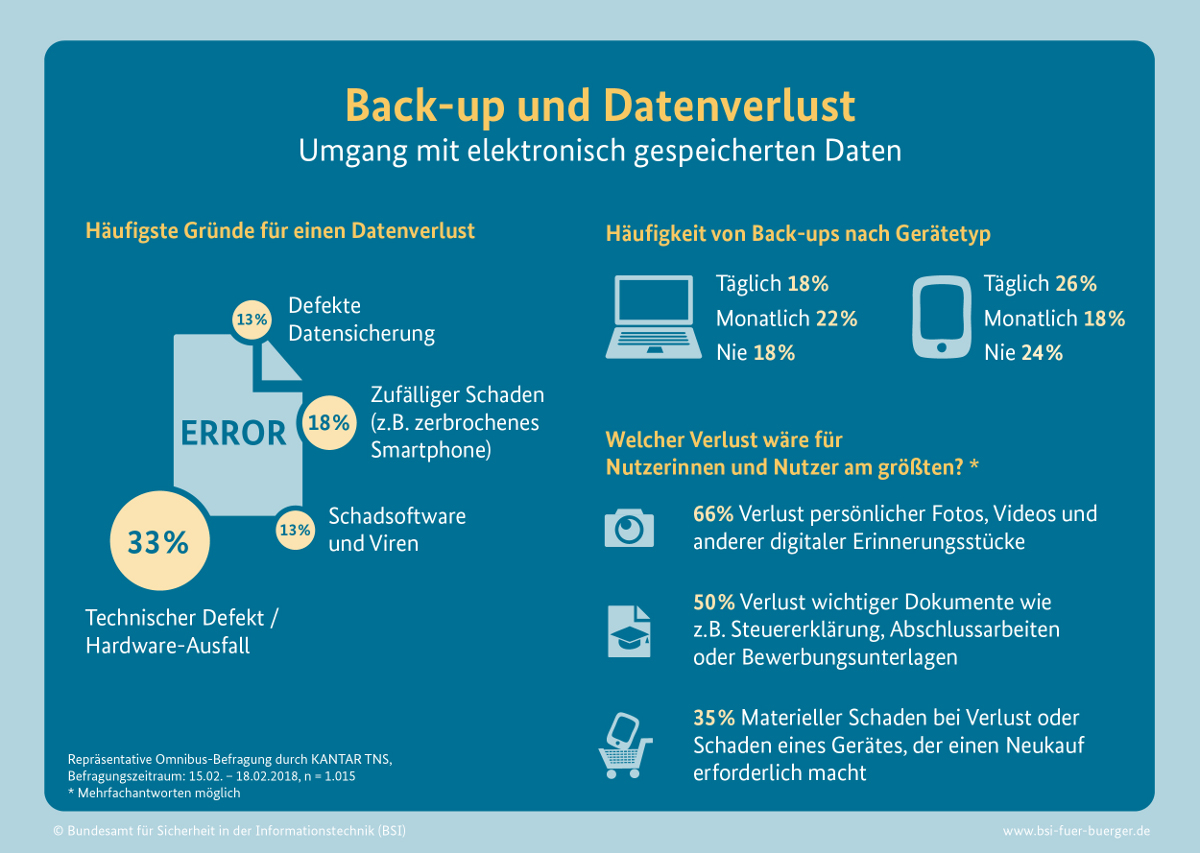
But the BSI survey also shows that 24% never back up. In the desktop area the number looks even worse. There it is with 18% still 6 percentage points less than with the small companions.
A functioning backup is one of the best security mechanisms of all and is a must with every recommendation in the area of prevention. The World Back up Day is therefore a good opportunity to deal with security.
The data protection can be increased at will.
As long as it is available!
At the end of an incident it counts that a working backup is available. The GitLab incident from 2017 shows that even five backups are not enough to get back into production. In that case, none of the variants worked fast and well. In order to avoid this fate, it is necessary to test the created backups. But also the saving and filing of the data should be done strategically. In the private sector one of the following variants is suitable:
- The backup on your own hard disk
Data is saved on the same hard disk. This is the worst way to make a backup. Helps to restore individual files. If the device is lost or the data is encrypted by ransomware, the backup is useless.
- A back up on external media
The data is under our own control. Against most scenarios this variant of data backup helps. Encryption Trojan or theft? Not a problem. The external hard drive keeps the data ready for the next computer – then you can continue working. In the event of a fire, however, the hard drive is also likely to be burned. Then the chances of recovering data are poor.
- A data backup in the cloud
A cloud for your back up. A hard drive is not necessary. But a lot of trust! The data is stored on the provider’s servers via the Internet. The mostly free offer with limited storage space makes connecting additional hardware unnecessary. But the price, which often has to be paid annually, the great trust and the uncertainty about what exactly happens with the data, are deterrent.
If your data moves in a professional environment that is particularly worthy of protection, then compliance with the 3-2-1 strategy is recommended:
At least three copies of your data!
In addition to your individual data storage, two further data copies are to be created. This is mainly to reduce the probability of default. If you take the failure probabilities of the devices and multiply them by each other, you will obtain your actual risk of not being able to access your data after an incident. Using a simplified example, this means, for example
The hard disks have a failure probability of 1:100. If you have backed up your data twice, there is a risk of 1/100 * 1/100 = 10,000 not being able to access this data. With another copy of the data, you reduce this probability enormously: 1/100 * 1/100 * 1/100 = 1,000,000. This is the goal you want to achieve as a business person.
Store your media on at least two different media
To further reduce the risk of not being able to access data, you should not commit yourself to a storage medium. Most of the storage media are not even decades old. Therefore, it is generally difficult to estimate how they will behave after decades of storage. For professional data, for example, tape drives and external hard disks can be used. SD cards, CDs, DVDs and even floppy disks theoretically pass as second media.
Storage of a back up at another location
In order to be able to recover data in the event of a natural disaster, it is strongly recommended to use external providers to store another copy of the data. It is therefore essential that the data is not only backed up within the company’s own four walls, but also at an external location.
Our recommendation for the production of back ups
The most important step is to create a backup. When setting up the backup, it should be taken into account that this backup should also be encrypted. After all, the theft of the backup should not lead to the important documents falling into the hands of others. We also recommend that you back up on your own hard drives. In the best case, however, not just one backup, but several. The hard disks should never be stored together. This also reduces the probability of a total loss of data to a minimum.

